Azure Landing Zones: Foundation for Secure & Scalable Cloud Adoption

Moving to the cloud without guardrails is like taking off without a runway. Azure Landing Zones give your organisation that runway - an opinionated, repeatable environment where every workload lands with identity, networking, security, and governance already in place. Built on Microsoft’s Cloud Adoption Framework (CAF), a landing zone accelerates deployment, reduces rework, and enforces best-practice architecture from day one.
“A landing zone is the minimum viable product of your Azure estate - engineered to scale, secured by design, and governed by policy.”
This guide walks through the ten pillars of an enterprise-ready landing zone and the practical actions to implement each one.
Table of Contents
- What Is an Azure Landing Zone?
- Cloud Adoption Framework Alignment
- Management Groups & Subscription Design
- Identity Foundation
- Networking Topology
- Governance & Policy
- Security & Compliance
- Automation & IaC
- Operational Baseline
- Cost Management & FinOps
1 · What Is an Azure Landing Zone?
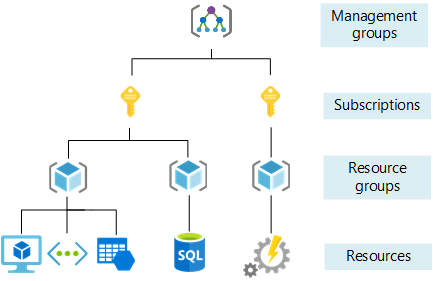
An Azure Landing Zone is a ready-made foundation for deploying workloads in the cloud. It gives you a structured, secure, and scalable environment where governance, identity, networking, and policies are already built in. It’s not a single resource or template. It’s a complete architectural approach that helps you start with best practices from day one.
The idea comes from Microsoft’s Cloud Adoption Framework. Landing Zones include key components like management group hierarchy, subscription design, access control, networking, tagging, cost management, and policy enforcement. The goal is to avoid one-off environments and give every team a shared and consistent starting point.
Instead of building everything from scratch every time, you deploy into a platform that’s already secured, organized, and ready to scale. That means fewer surprises, more automation, and faster time to value.
2 · Cloud Adoption Framework Alignment
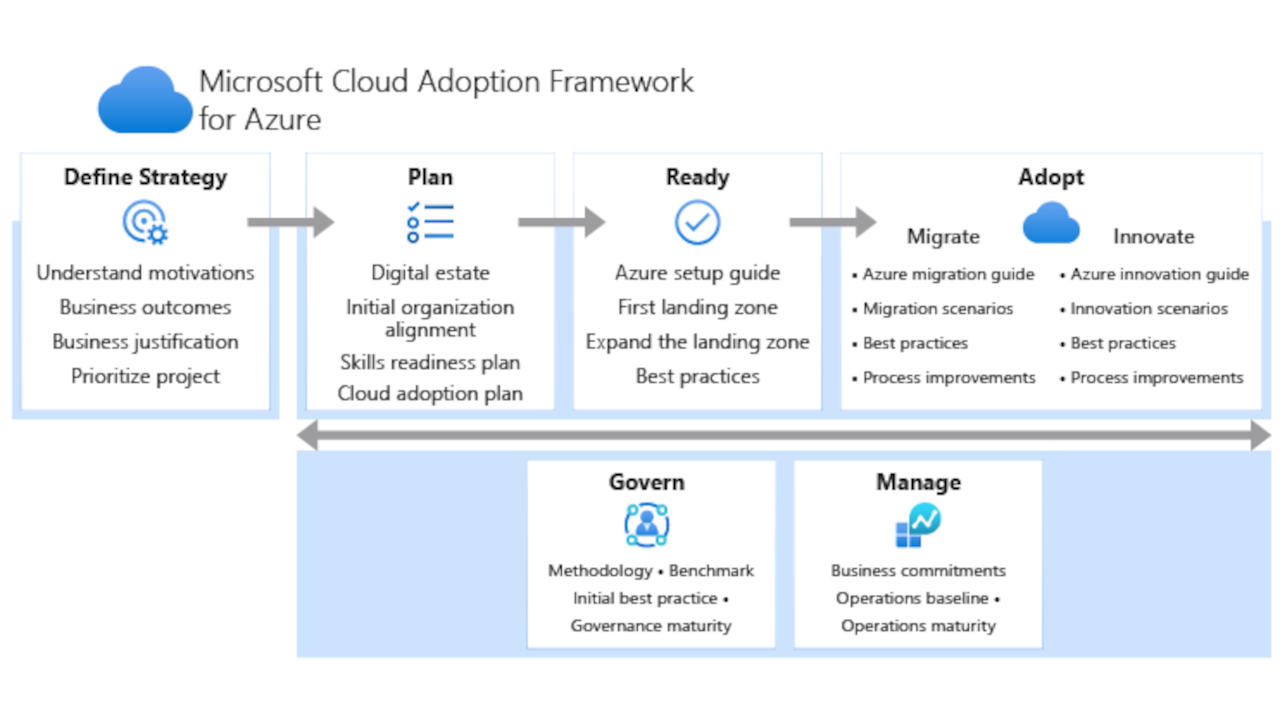
The Microsoft Cloud Adoption Framework (CAF) is the official methodology trusted by organizations across the globe to build cloud environments that are secure, governed, and scalable. It covers every step in the cloud journey. This includes defining business strategy, designing the architecture, deploying infrastructure, and enabling teams to manage it properly.
When you build a Landing Zone, you are applying the Ready phase of CAF. This phase includes setting up a clear management hierarchy, access control, network topology, policies, and workload separation. It provides a strong foundation that keeps your environment consistent, secure, and maintainable.
Microsoft offers ready-to-use templates for Landing Zones, based on best practices, using Bicep or Terraform. These are called Enterprise-Scale Landing Zones. They help you move fast while staying aligned with CAF principles. This includes tagging, cost control, monitoring, and automation.
One of the biggest benefits of CAF is flexibility. It helps you build your cloud environment in a way that is not tied to a specific vendor or partner. Even if you switch integrators in the future, your platform remains clean, documented, and fully supported.
📘 Official Microsoft documentation: Cloud Adoption Framework
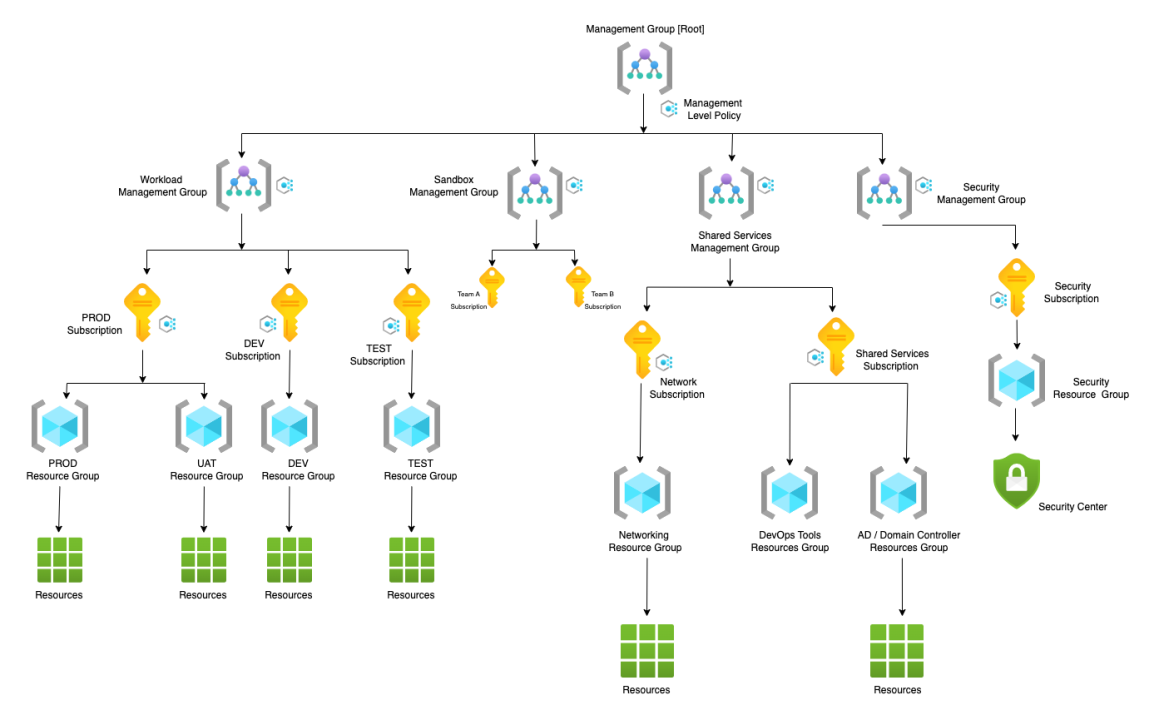
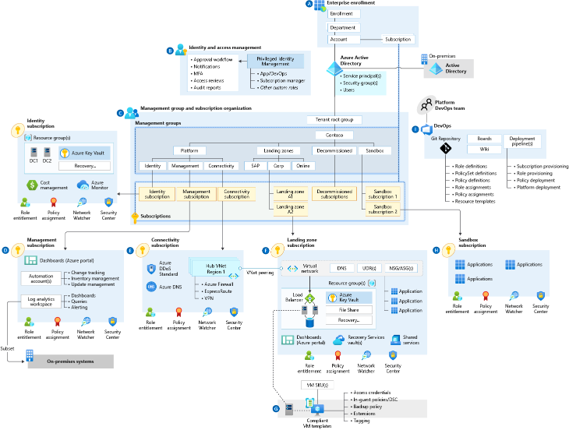
3 · Management Groups & Subscription Design
One of the core principles of an enterprise-grade Azure environment is a well-structured management group and subscription hierarchy. It enables consistent governance, cost tracking, policy enforcement, and access control across all workloads.
Start by creating a tiered management group structure. A common pattern is:
Tenant Root → Platform → Landing Zones → Prod / NonProd.
This allows you to apply policies and RBAC roles at the highest relevant scope, so that every child management group or subscription inherits the right guardrails automatically.
Separate your core platform resources — such as shared networking, DNS, identity, monitoring, and firewalls — into a dedicated Platform management group and subscription. Workload-specific environments, like apps or data platforms, should reside in Landing Zone subscriptions underneath.
Subscription boundaries should reflect your organization's business domains, regulatory compliance requirements, or lifecycle stages. For example, separate subscriptions for production and non-production ensures isolation and prevents accidental impact.
Apply consistent tagging across subscriptions, using keys like CostCenter, DataClass, Environment, and Owner. This improves cost visibility, chargeback, and security classification.
📘 Official Microsoft documentation: Management Group and Subscription Organization – Microsoft Docs
4 · Identity Foundation
Identity is the new security perimeter. A strong identity foundation is critical to securing any Azure environment. Every Landing Zone should rely on a centralized and well-managed Microsoft Entra ID (formerly Azure Active Directory) tenant.
Enforce Multi-Factor Authentication (MFA) across all users. Define Conditional Access policies based on user role, device compliance, location, and risk signals. Block legacy authentication protocols to reduce attack surfaces.
Use Privileged Identity Management (PIM) to enforce just-in-time elevation for admin roles. No user should have standing global admin rights. Instead, temporary access should be granted with approval and auditing.
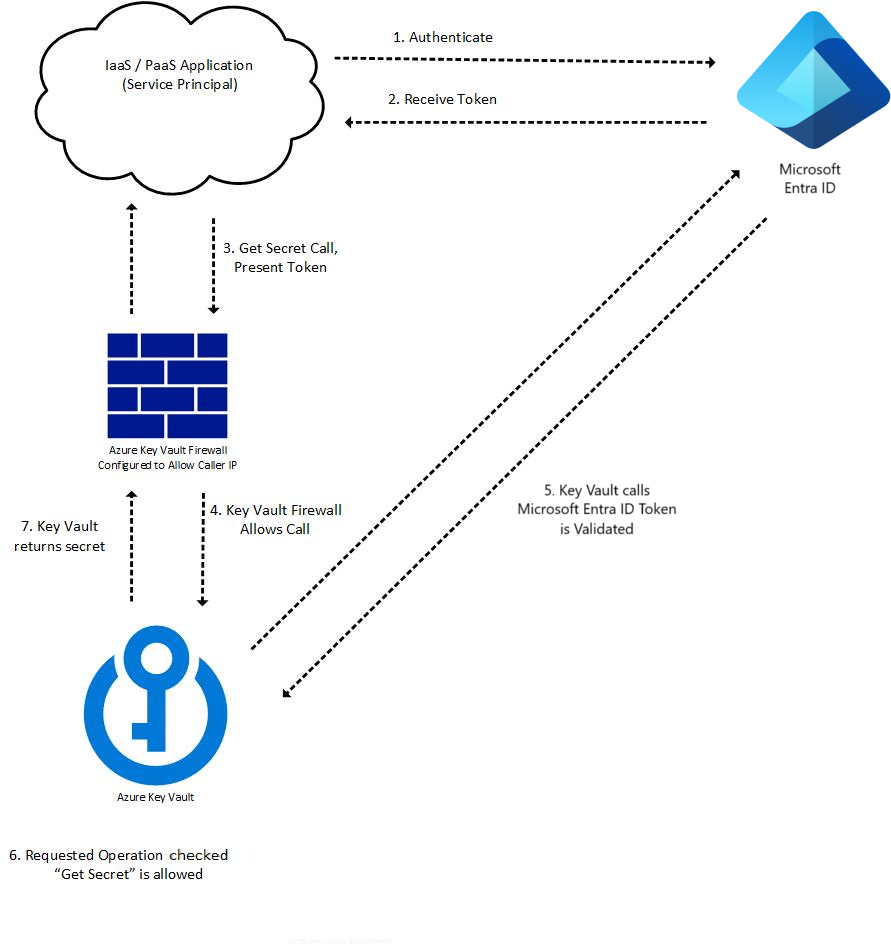
Applications and workloads should never store secrets in code. Use managed identities and service principals integrated with Azure Key Vault to access resources securely. This minimizes key exposure and supports proper lifecycle management.
In complex environments, centralize identity using cross-tenant B2B or synchronize hybrid users with Microsoft Entra Connect. Ensure role-based access control (RBAC) is assigned to groups, not individual users, for easier management.
📘 Official Microsoft documentation: Identity and Access Management – Microsoft Docs
5 · Networking Topology
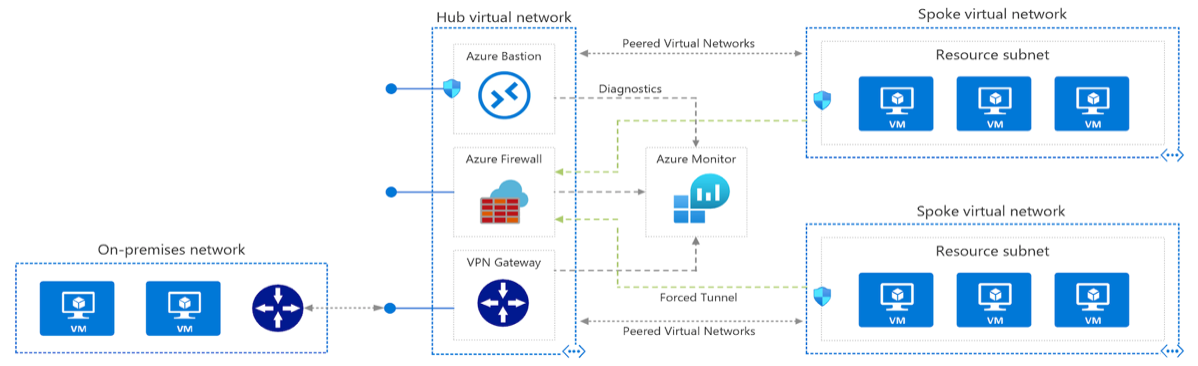
A well-designed network topology is critical to maintaining security, scalability, and operational clarity in Azure. The most recommended pattern is the hub-and-spoke architecture, which provides centralized control while supporting workload isolation.
In this model, the hub virtual network serves as the central connectivity and security layer. It typically hosts shared services such as Azure Firewall, DNS, Bastion, NAT Gateway, and third-party Network Virtual Appliances (NVAs).
Spoke virtual networks are used for specific workloads, environments, or business units, and are connected to the hub using VNet peering.
All traffic between spokes - or between spokes and on-premises - is routed through the hub. This allows you to apply consistent security controls, traffic inspection, and egress policies. When internet-bound traffic is forced through the hub, Azure Firewall Premium or third-party IDPS solutions can inspect it before allowing it out.
To reduce your attack surface, use Private Endpoints and Private DNS Zones instead of public access to Azure PaaS services. This ensures that traffic stays inside the Microsoft backbone network and never exposes public IPs.
For hybrid connectivity, use Azure Route Server, VPN Gateway, or ExpressRoute. These options allow dynamic routing between your on-premises network and Azure and support scenarios like BGP propagation, MPLS integration, and branch connectivity.
📘 Official Microsoft documentation: Hub-and-Spoke Architecture - Microsoft Docs
6 · Governance & Policy
Governance is the backbone of any cloud environment. In Azure, it allows you to define rules and boundaries that keep your environment secure, compliant, and consistent - without relying on manual processes. At the heart of this model are Azure Policy and Policy Initiatives.
Define a centralized set of policy initiatives that enforce your organisation's standards. These should include:
- Tag compliance - require tags like
Environment,Owner, andCostCenteron all resources. - Resource naming rules - enforce consistent naming conventions across the platform.
- Location restrictions - allow only approved regions such as West Europe or North Europe, based on data residency or compliance.
- SKU restrictions - block unsupported or expensive VM sizes and enforce disk encryption.
- Secure deployment templates - use Bicep modules or Azure Blueprints to deploy baseline environments with built-in security and guardrails.
Use Azure Policy remediation tasks to automatically fix non-compliant resources. For example, if someone deploys a resource without the required tags, the policy engine can apply them retroactively.
This approach ensures that even in fast-moving development environments, your cloud remains under control, audit-ready, and aligned with corporate standards.
📘 Official Microsoft documentation: Azure Policy - Microsoft Learn
7 · Security & Compliance
Security is not something you add at the end. It must be embedded into every layer of your Azure Landing Zone. From identity to infrastructure, every component should be protected by default and monitored continuously.
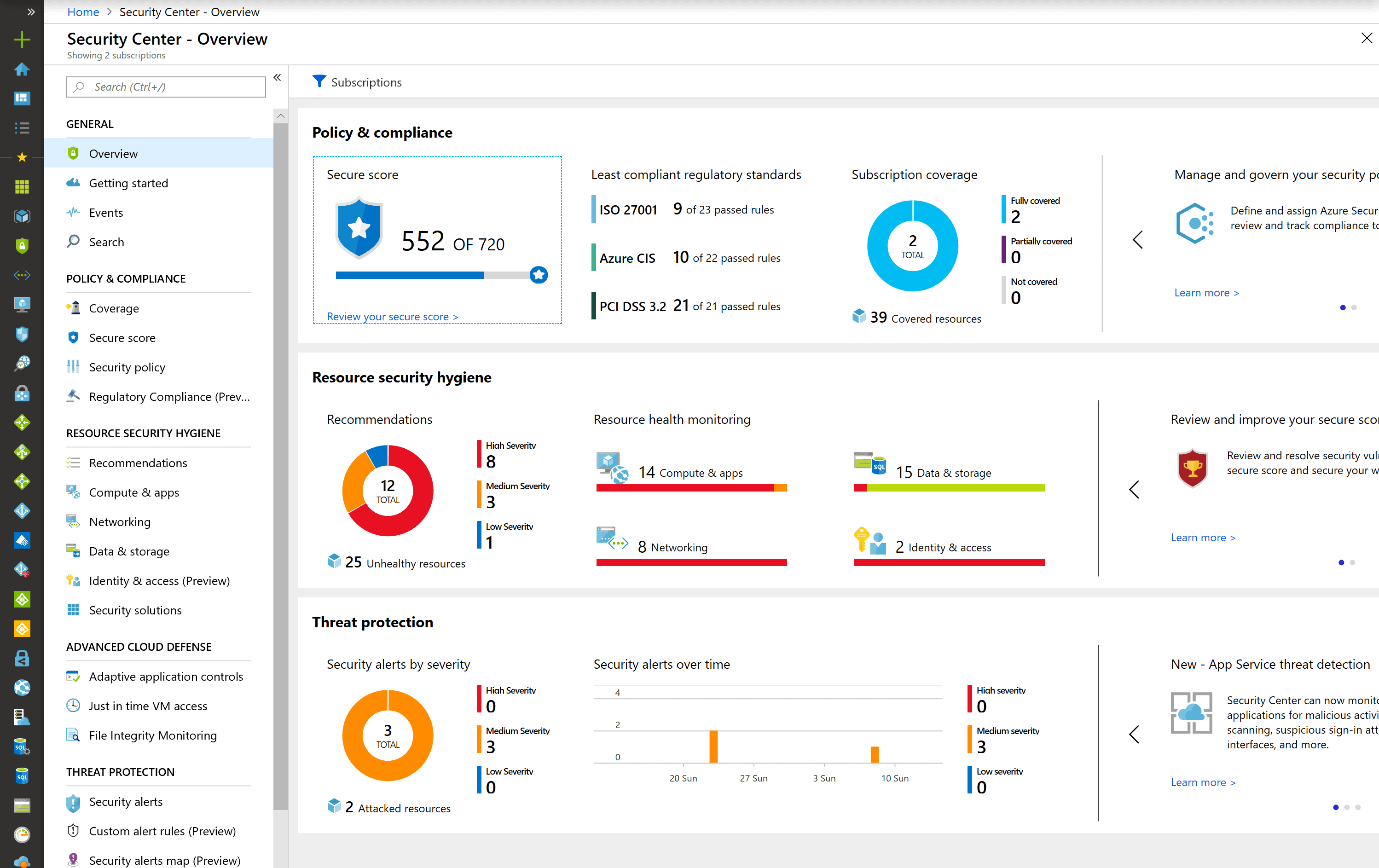
Start by enabling Microsoft Defender for Cloud across all subscriptions. It provides threat detection, posture management, and security recommendations tailored to your environment. Use the built-in Secure Score to measure and track improvements.
For centralized threat detection and automated response, deploy Microsoft Sentinel in your management subscription. It acts as a full SIEM and SOAR platform that ingests signals from Azure, Microsoft 365, Defender, and even third-party systems. Sentinel supports advanced analytics, custom playbooks, and incident investigation.
Use the Regulatory Compliance dashboard in Defender for Cloud to map your environment against standards such as CIS, NIST, or ISO 27001. This helps teams understand where gaps exist and which remediations are most critical.
For highly sensitive workloads, use Azure Key Vault Managed HSM or Azure Confidential Computing. These services protect encryption keys with hardware-level security and ensure data is protected even during processing.
📘 Official Microsoft documentation: Azure compliance documentation- Microsoft Docs
8 · Automation & IaC
Every Landing Zone should be treated as code. This means your entire Azure environment - from resource groups and networking to policies and role assignments - must be defined, versioned, and deployed using Infrastructure as Code (IaC).
Microsoft recommends using Bicep or Terraform as declarative IaC tools. Store the code in GitHub or Azure Repos and run CI/CD pipelines to validate and deploy it across environments in a consistent way.
For Bicep, compile and deploy with commands such as:
az bicep build then
az deployment sub create --location westeurope --template-file main.bicep
In Terraform pipelines, run terraform plan and terraform apply, using remote state and locking to avoid conflicts.
Test compliance regularly with:
az policy state trigger-scan
This detects drift and keeps configurations aligned with your baseline.
Automate drift detection and remediation on a schedule with GitHub Actions, Azure DevOps, or Logic Apps.
📘 Official Microsoft documentation:
Infrastructure as Code (IaC) - Microsoft Docs
9 · Operational Baseline
A Landing Zone is never “done” - it must be operated, supported, and continuously monitored. A solid operational baseline keeps the platform resilient, observable, and ready for recovery.
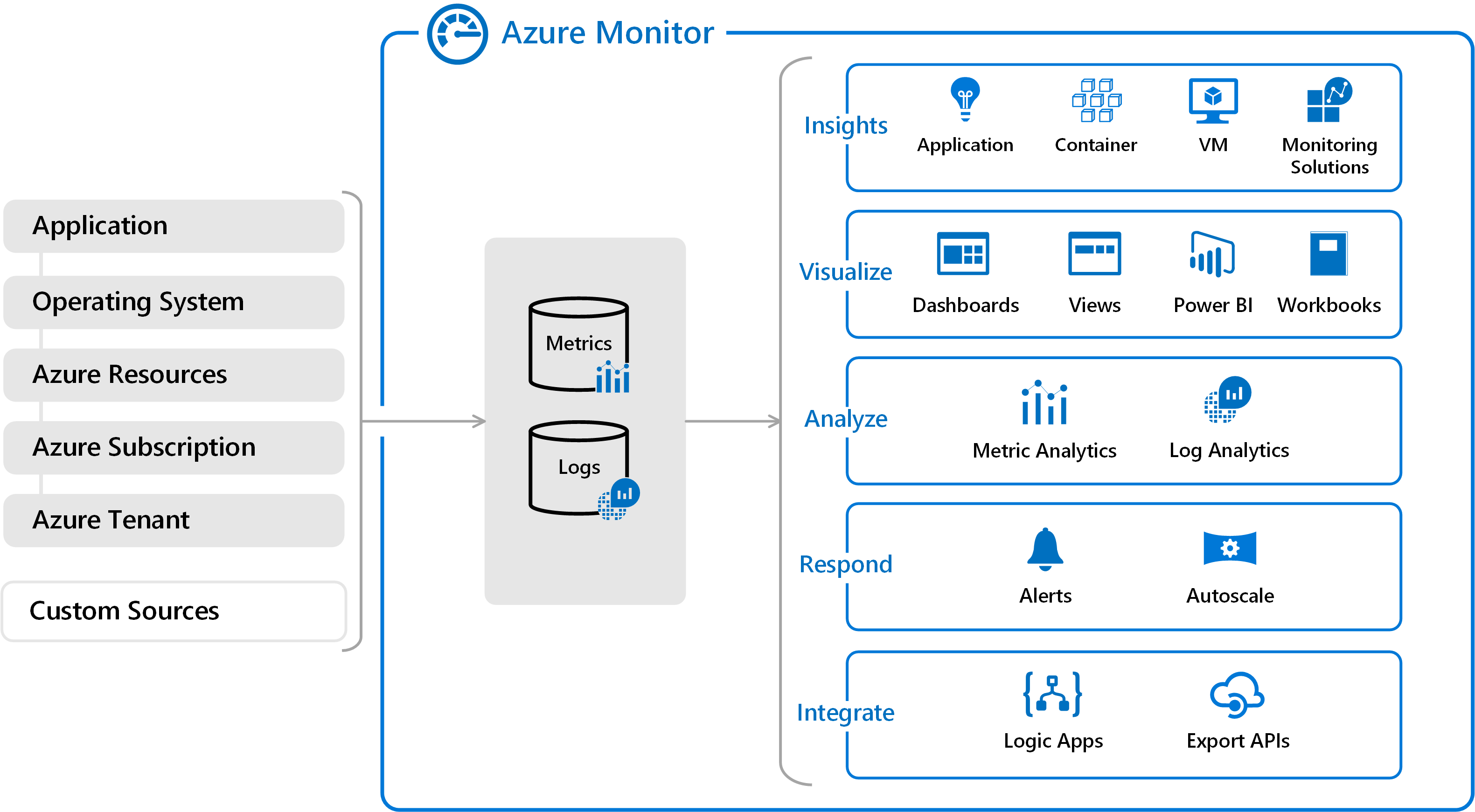
Deploy a central Log Analytics Workspace in each region and use Data Collection Rules (DCRs) to funnel the right telemetry to the right workspace, optimising cost and visibility.
Protect critical workloads with Azure Backup vaults and Azure Site Recovery. Set your Recovery Time Objective (RTO) and Recovery Point Objective (RPO) to match business requirements.
Build Azure Monitor dashboards that show workload health, cost usage, policy compliance, and security posture so the ops team can act fast.
Standardise alert routing with Action Groups. Send notifications to ServiceNow, Teams, email, or trigger Logic Apps for auto-remediation.
📘 Official Microsoft documentation:
Azure Monitor - Microsoft Docs
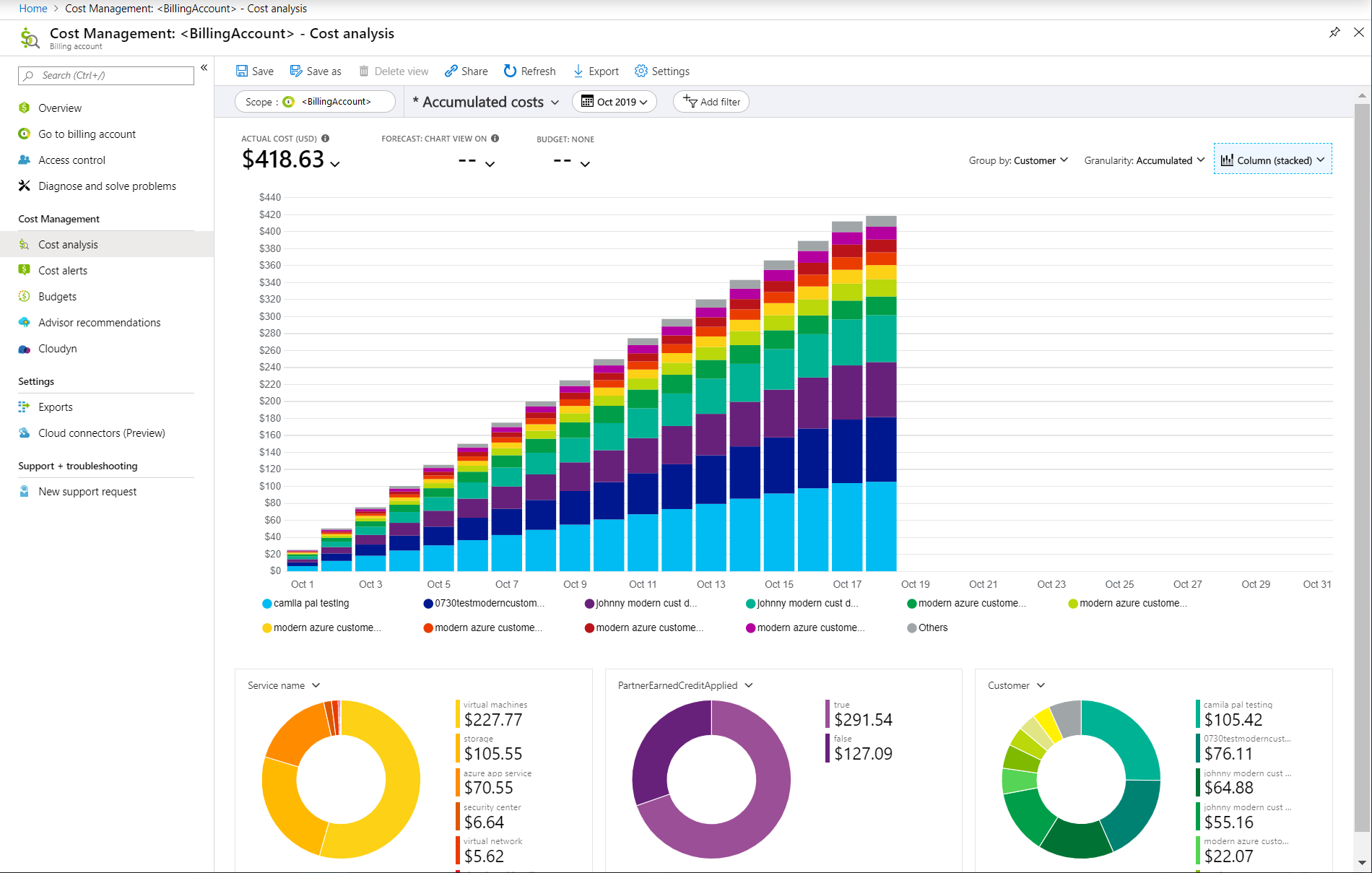
10 · Cost Management & FinOps
FinOps is not an afterthought - it must be designed into your Landing Zone from the beginning. Without cost visibility and accountability, even the most secure and scalable environment will become unsustainable.
Start by separating production and non-production workloads into different subscriptions. This allows for clean chargeback, cost reporting, and budget enforcement per business unit or environment.
Make tagging mandatory. Use tags like CostCenter, Environment, Owner, and Project to segment spend and filter reports. Enforce tagging with Azure Policy and monitor compliance regularly.
Set up budgets and anomaly alerts at both the subscription and tag level. This helps identify unexpected spikes in real time and prevents budget overruns.
Review Azure Advisor cost recommendations every month. These include right-sizing VMs, deleting unused resources, and adopting Reserved Instances or Savings Plans where appropriate.
📘 Official Microsoft documentation:
Azure Cost Management - Microsoft Docs
FinOps in Azure - A Practical Guide
Conclusion
An Azure Landing Zone is not just a deployment framework - it is a long-term investment in operational excellence. By aligning with the Microsoft Cloud Adoption Framework, codifying best practices, and embedding governance and automation from day one, you ensure that every workload runs on a secure, scalable, and maintainable foundation.
Whether you are a startup scaling rapidly or an enterprise modernising legacy systems, a well-designed Landing Zone accelerates your cloud journey and reduces risk. It lets teams focus on innovation rather than infrastructure while keeping full control and compliance.
Build your Landing Zone once and let it serve as the launchpad for your entire cloud strategy - no matter how large your ambitions become.
📗 Read more from Captain Azure:
FinOps in Azure - A Practical Guide
